In today's scenario, we are seeing a shift from the monolithic landscape to microservice landscape. In simple words it can be termed as breaking a complex problem into smaller parts and making it easier to manage and develop. In Go to make this easier there is a framework GO MICRO - a helpful framework for building microservice applications with the Go programming language.
Why Microservice Architecture
Imagine a library where all the books used to be stacked in one massive room. It would be chaotic trying to find the book you needed among the towering shelves. But now, picture this library transformed into a series of smaller rooms, each dedicated to a specific genre—mystery, romance, science fiction, and so on. Each room is organized neatly, making it easier for readers to find the books they're looking for without getting lost in the sea of literature. This is similar to how microservices work in software—they break down complex applications into smaller, specialized components, making it simpler for developers to manage and maintain the software.
Now how do we build them??
Meet GOMICRO - A framework for distributed systems development
In the world of microservices, Go Micro is like your trusty sidekick. It helps developers build and manage microservices without all the headaches of doing it from scratch. Think of it as a toolbox full of handy tools to make building microservices easier and faster.
How Go Micro helps us??
-
Authentication and Authorization - Security is paramount in any architecture.Gomicro provide authorization.It seamlessly integrates with authentication providers like Keycloak, serving as a middleware to authenticate incoming requests.
-
Service Discovery - Effective communication among microservices necessitates a reliable service discovery mechanism. Go Micro simplifies this with built-in support for mdns (Multicast DNS) and offers integrable libraries (plugins) for popular options such as Eureka, Etcd, Consul, and NATS, among others.
-
Messaging - Messaging is an important aspect in the microservice architecture and event driven architectures. Go Micro eases the implementation of pub-sub models and other messaging paradigms with its plugin-based approach. Whether it's HTTP event message brokering or support for NATS, RabbitMQ, or Kafka, Go Micro has you covered.
-
Protocols - Go Micro supports communication via HTTP and RPC (Remote Procedure Call), providing abstractions for synchronous communication. This flexibility enables developers to choose the most suitable communication protocol for their specific use cases.
Tutorial
-
Visit WeDAA: Go to WeDAA.
-
Choose GoMicro Application: Navigate to the service tab in the sidebar and select Go. Drag and drop it onto the canvas.
-
Connect a Database and Add Authentication: Connect a database to the application. Additionally, add authentication to secure the application. WeDAA supports Keycloak as an authentication IDP.
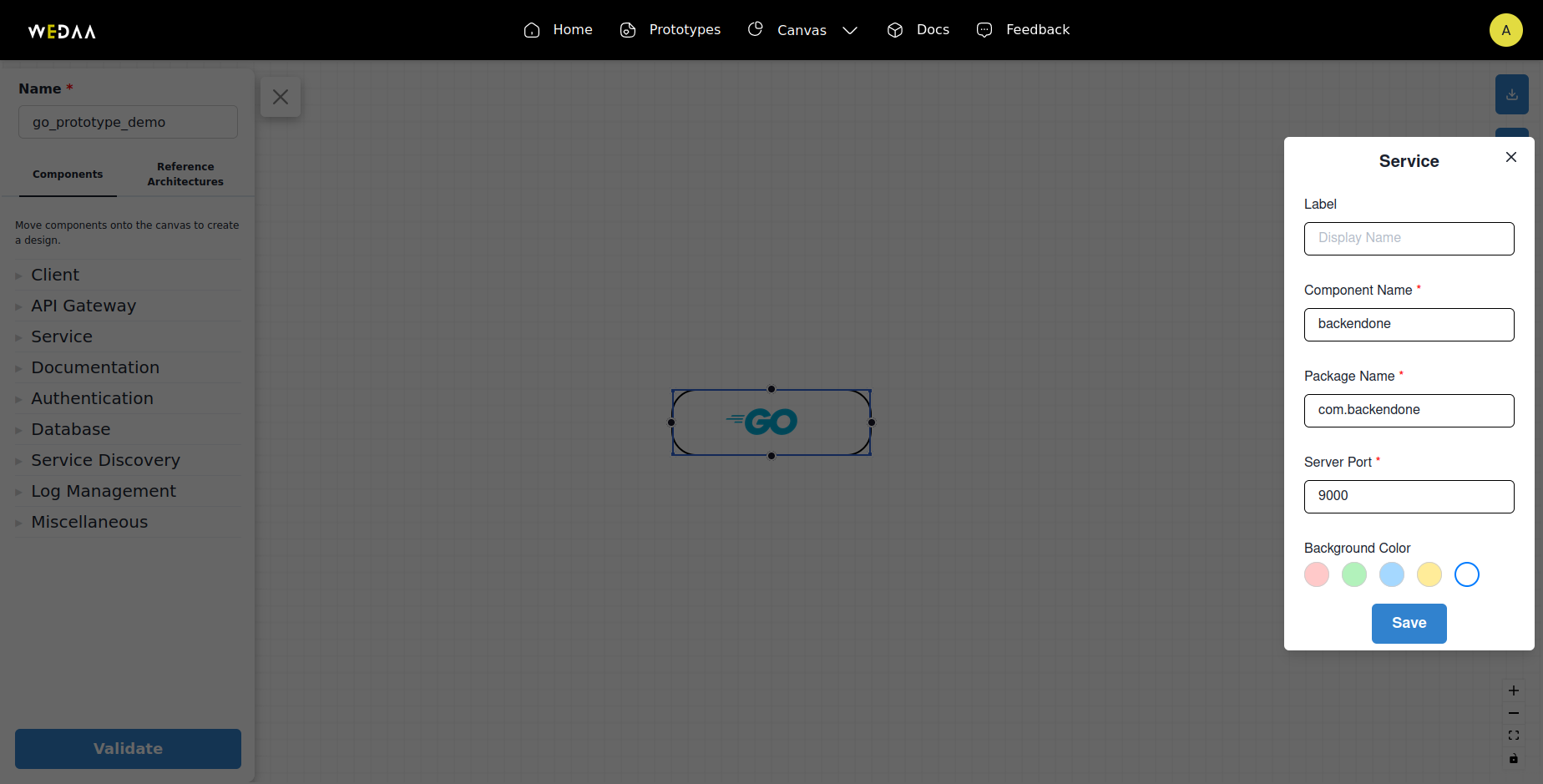
- Fill in Required Details: Provide necessary details for the service and database connection.
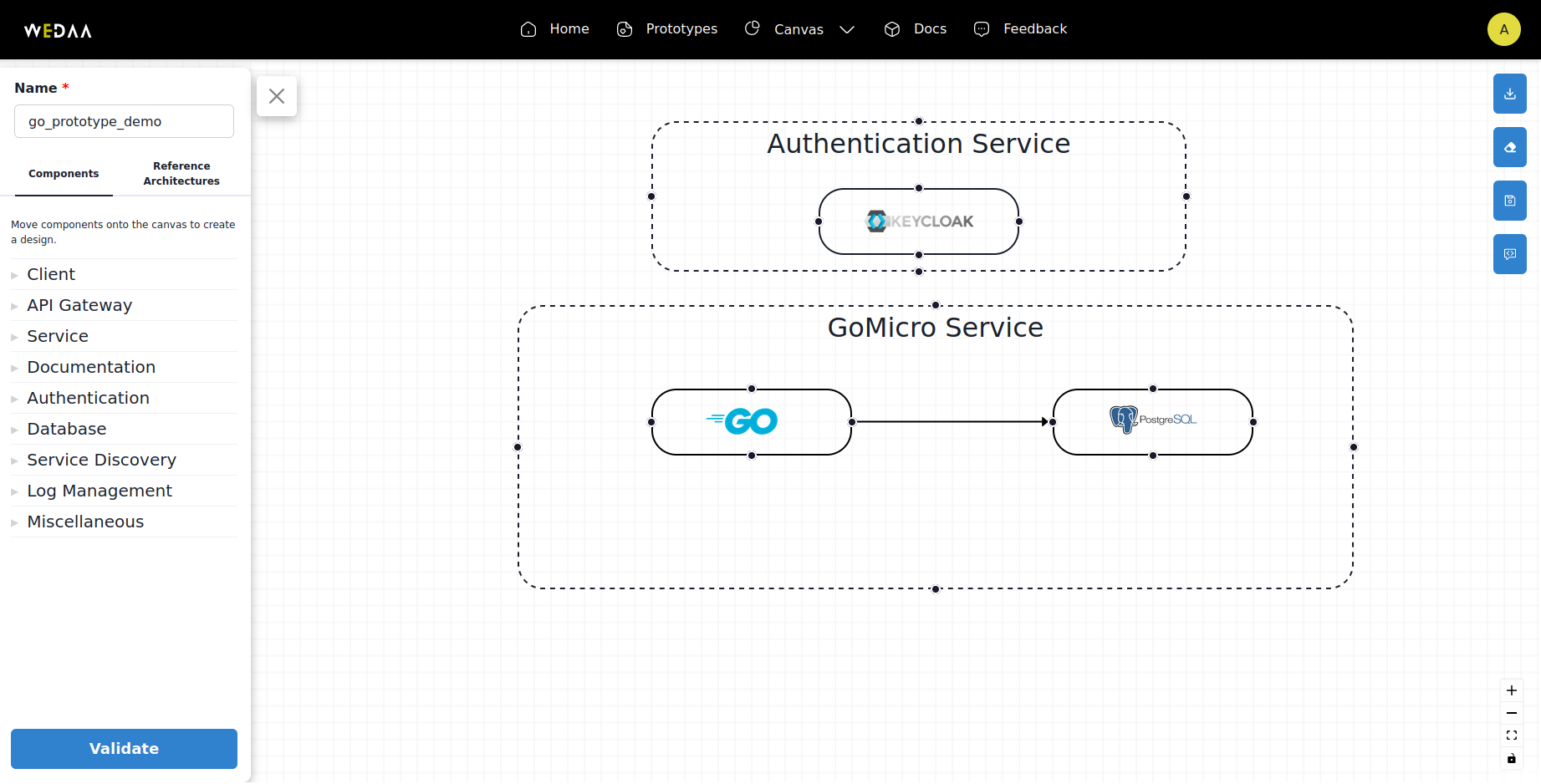
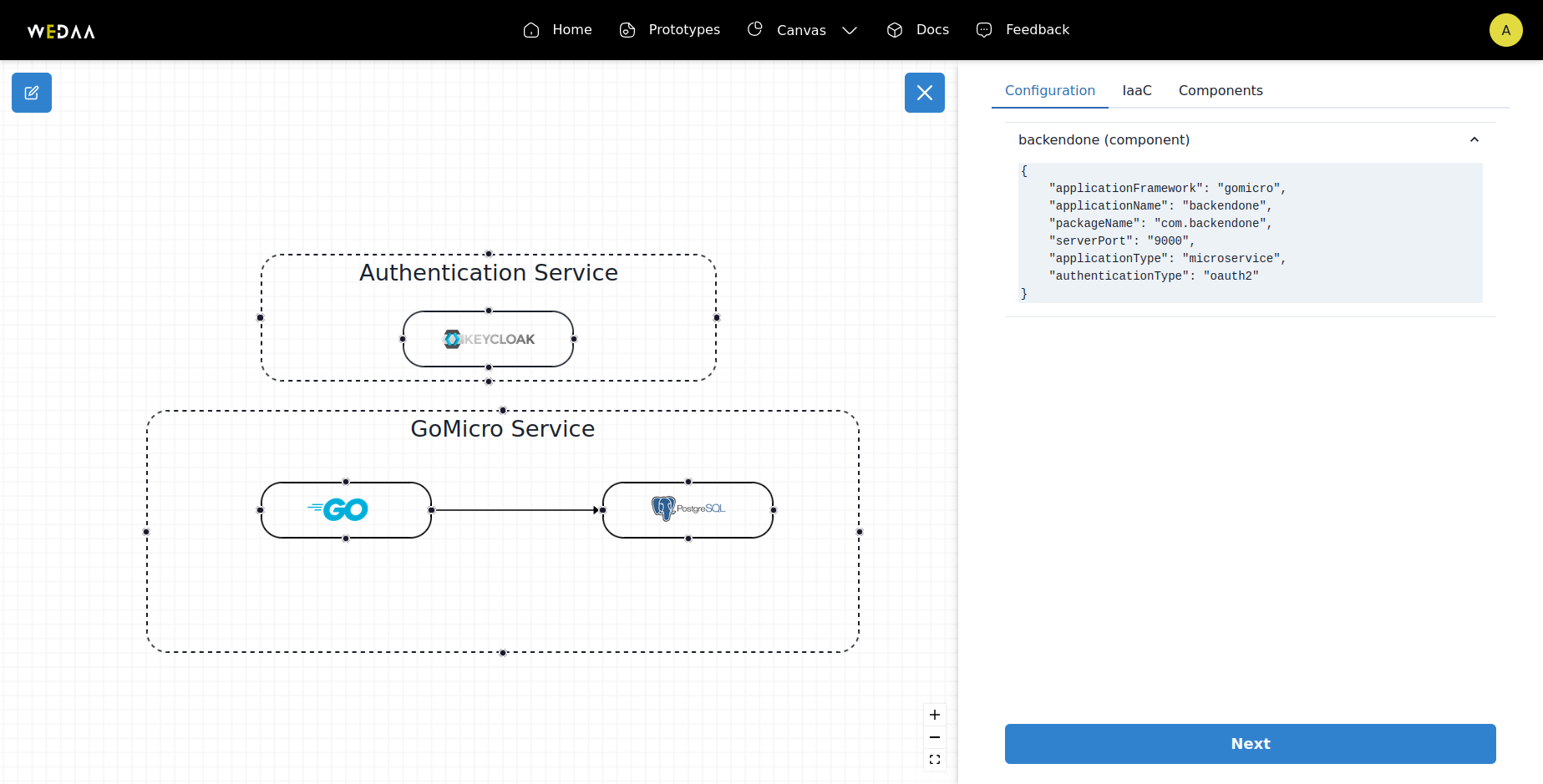
- Validate and Review: Click on validate to review the setup. Ensure everything is configured correctly.
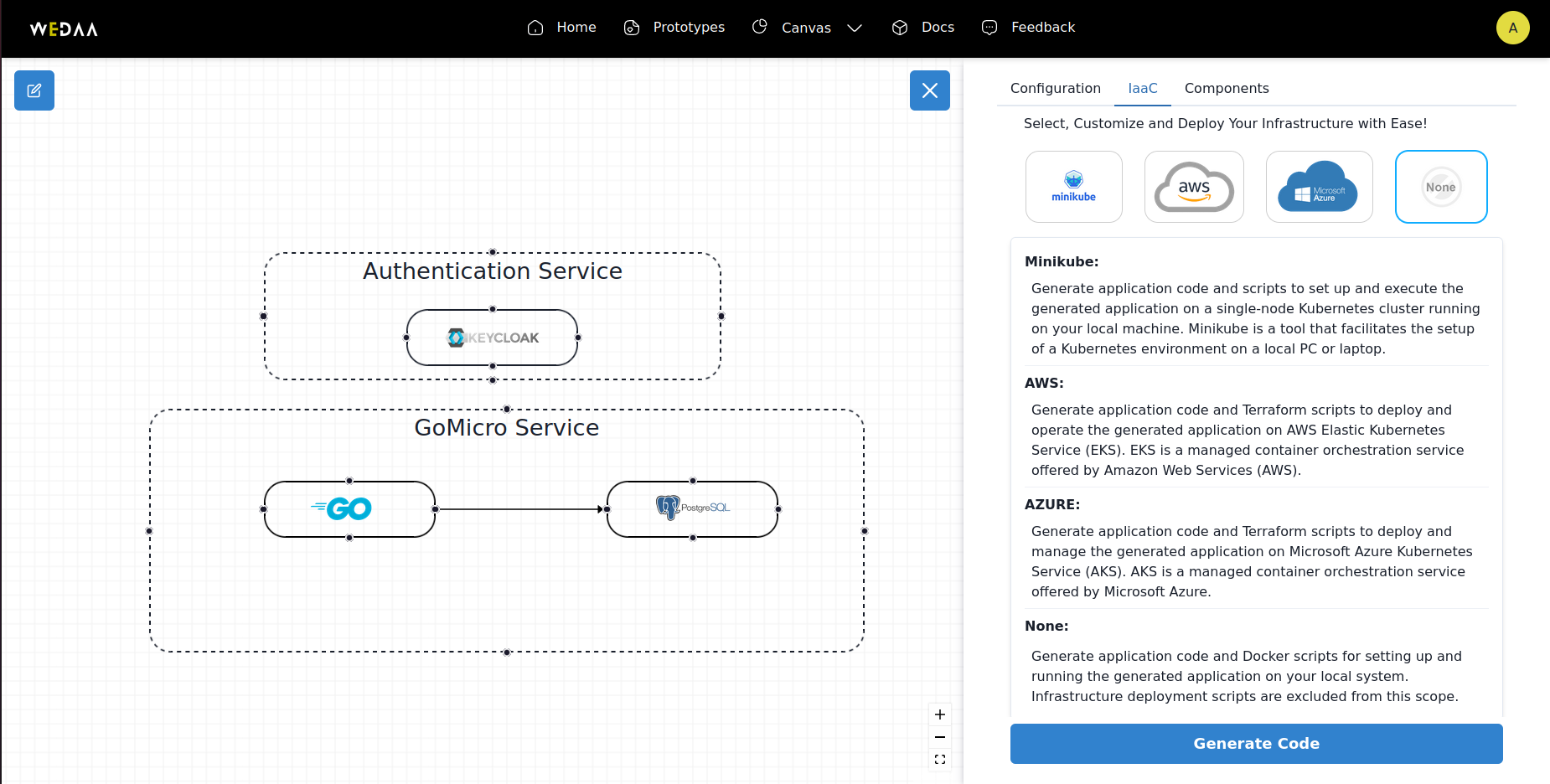
- Cloud Service Setup (Optional): Weeda has support for Azure, AWS and minikube.We can opt for one and fill in the necessary details to deploy applications in the specific cloud provider.we can skip this step for now by selecting none.
- Generate Project Zip: After submission, a zip file containing the project will be generated.
Application Quickstart Guide
-
Prerequisites: Ensure Docker is set up in advance if Keycloak is not configured as standalone or if PostgreSQL is not set up separately. Keycloak and PostgreSQL provided are Dockerized containers.
-
Start Keycloak and PostgreSQL:
docker compose -f docker/keycloak.yml up -d
docker compose -f docker/postgresql.yml up -d
-
Start the Go Service: Once Keycloak and PostgreSQL services are up, start the Go service.
-
Install Dependencies and Run the Service:
go mod tidy
go run .
This command will install any required dependencies and then run the Go service.
Understanding the code
package main
func main() {
app.Setconfig()
migrate.MigrateAndCreateDatabase()
auth.SetClient()
config.InitializeDb()
port :=app.GetVal("GO_MICRO_SERVICE_PORT")
srv := micro.NewService(
micro.Server(mhttp.NewServer()),
)
opts1 := []micro.Option{
micro.Name("backendone"),
micro.Version("latest"),
micro.Address(":"+port),
}
srv.Init(opts1...)
r := mux.NewRouter().StrictSlash(true)
r.Use(corsMiddleware)
registerRoutes(r)
var handlers http.Handler = r
if err := micro.RegisterHandler(srv.Server(), handlers); err != nil {
logger.Fatal(err)
}
if err := srv.Run(); err != nil {
logger.Fatal(err)
}
}
-
Config Initialization - The application begins by loading configuration values from externalized YAML files into the environment. This ensures that the application has access to the necessary configuration parameters.
-
Database Migration - WeDAA supports migration for PostgreSQL databases. Using the go-migrate package library, a new database is created and data initialization is performed. This ensures that the database is properly set up and populated with initial data.
-
Authentication Setup - The code proceeds by setting up the authentication client,here Keycloak is being used as the identity provider (IDP) for authentication. This involves establishing a connection to Keycloak.
-
Microservice Setup - The micro.NewService function is a notation used by GoMicro to set up the microservice. Here, configurations are provided to the microservice via options. This step initializes the microservice and prepares it to handle incoming requests.
-
Router Setup - The code utilizes the mux router to create a routing setup. This involves defining endpoints and their corresponding handlers. The router is then registered with GoMicro, indicating that the microservice should use this router to handle incoming requests.
-
Application Execution - Finally, the application is run. This step starts the microservice, allowing it to listen for incoming requests and handle them according to the defined routing setup.
Conclusion
Go Micro leverages Go interfaces for each distributed system abstraction, rendering them pluggable and runtime-agnostic. This inherent flexibility allows developers to seamlessly integrate various underlying technologies, optimizing microservice development in a clean and efficient manner.